Easyrec is an open source recommender engine which can be trained and customized to provide personalized recommendations using REStful Web Service.
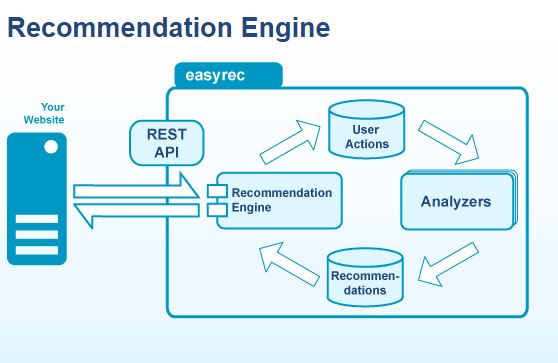
Easyrec exposes its functionality through REST API which provides several interaction types:
Actions
- view
- buy
- sendaction
Recommedations
- other users also viewed
- other users also bought
- items rated good by other users
- recommendations for user
- related items
- action history for user
Community Rankings
- most viewed items
- most bought items
- most rated items
- best rated items
- worst rated items
The list of recommendations is returned in XML and JSON notation to be further processed by your web application.
Easyrec API can be accessed from its main website http://easyrec.org/ or could be installed alongside with the web application on your own server. Easyrec require at least Java 1.5 and MySQL server for its functionality.
Download easyrect from: http://easyrec.org/recommendation-engine