You can actually send Telegram message from command-line interface / bash in Linux using an unofficial “telegram-cli“ client by Vitali Valtman (vysheng)
Obtaining and Compiling telegram-cli
But first, before sending telegram messages, you need to build the client. You may start by installing its dependencies
sudo git apt-get install libreadline-dev libconfig-dev libssl-dev lua5.2 liblua5.2-dev libevent-dev libjansson-dev libpython-dev make
Then, you can get the latest telegram-cli client from vysheng GitHub
git clone --recursive https://github.com/vysheng/tg.git && cd tg
Afterwards, you may configure ‘telegram-cli’ and compile it
./configure make
Alternative Download
Alternatively, you can download Telegram source code from my server:
Running telegram-cli
After finished compiling telegram-cli, you may try and start using telegram.
bin/telegram-cli -k tg-server.pub
For first time use, you may need to key in the authorization code, the code will be sent to your mobile device to allow ‘telegram-cli’ to log as your username.
bin/telegram-cli -u -k tg-server.pub
In my experience you may need to replace the +[country_code] phone-number with ’00’. so if your phone number includes country code is +60123456789, then you must replace it with 0060123456789 (however, your mileage may vary.
bin/telegram-cli -u 00123456789 -k tg-server.pub
Once the authorization CODE has been entered, you are free to use telegram. Telegram use the concept of ‘peer’ (contact) to send messages instead of phone number. So in order to get a list of your peer, you need to run “contact_list” command.
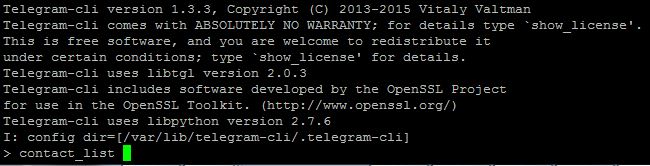
> contact_list John_T_Doe Jane_doe_2 Warrick_Brown Mark_Nelson
To send message to a peer/contact (for example to Warrick Brown), just type
> msg Warrick_Brown "wassup, dude? want to hang out today?"
To quit, you can type
#telegram-client > safe_quit
NOTE: IF YOU FAIL TO COMPILE TELEGRAM FROM GITHUB
If you find it difficult or failed to compile telegram-cli from GitHub, then you can download this telegram-cli source code from my server which is tested to compile under Raspbian Jessie, Debian Jessie, Ubuntu 14.04 LTS and Ubuntu 16.04 LTS.
Alternative Telegram source code: