DKIM (Domain keys identified Mail) is a scheme for which allows a receiver to verify that the email originated (or authorized) by the domain’s owner via a digital signature.
Having DKIM signature adds credibility to the email messages sent from the origin host/domain, which is crucial for automated emailing system to avoid the messages from being suspected as SPAM email or spoofed email.
I managed to set up DKIM for an academic journal website which I’ve managed. The journal’s runs on Open Journal System web application, the addition of DKIM is crucial to avoid GMail or Microsoft Live from labeling the automated emails sent from the academic journal from being labeled as spam.
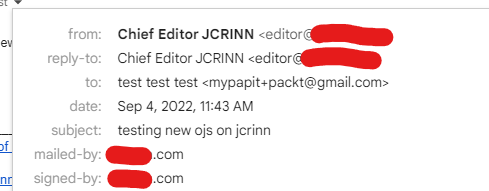
At first I found that the DKIM scheme that I’ve setup was running fine and the email messages was verified correctly from my Organizational email domain. However, I’ve noticed a problem when the automated email sent from OJS is not properly verified by Gmail-addressed account (@gmail.com). Upon inspection in the email header, I’ve noticed that the GMail marked the DKIM signature sent from my domain as “bad format”. Example below:
DKIM: 'FAIL' with domain jcrinn.com
dkim=neutral (bad format) header.i=@example.com header.s=mail header.b=AbCdE5g;After hours of searching and debugging, including referring to the DKIM NS TXT record for reference, I finally found out that Gmail treat the “g=*” optional parameter as required, and thus I’ve to append “;g=*” to the DKIM TXT record on my domains’ DNS record.
So it become similar like this:
TXT default._domainkey v=DKIM1; p=yourPublicKeywHiCHi5+abit+1OnG; g=*After altering the records, it seems GMAIL finally able to verify the automated emails sent from my OJS-based web application
Hopefully this will work out fine for you too!
P/S: DigitalOcean has an excellent tutorial on DKIM installation and setup in GNU/Linux operating system.